Understanding the Concept of Google Cloud Identity Platform
Posted July 21, 2023

The power of identity platforms (IdP) from the cloud has created reliable and sustainable IDaaS Vendors. The Google Cloud Identity Platform (GCP) is an IDaaS solution from Google that centrally manages our users and teams. In this article, we will explore the GCP identity platform, how to get it, and how it compares to other identity and access management solutions while answering questions such as, is GCP an identity provider? Is Google IdP free?
Cloud-based services are increasingly becoming the new digitally driven IT adoption strategy. With data stored and processed in the cloud, securing that data is a must keep in check when managing cloud IT resources. Identity and access management lets the appropriate users and teams within an organization be granted access to the right resources. Data security posture management (DSPM) is a must for organizations. IDaaS is a major champion for observing cybersecurity threats for cloud-based identity Security.
IDaaS solutions provide automatic, long-term security that accurately identifies, authenticates, and authorizes users. These systems leverage access privileges to restrict unauthorized users from accessing sensitive information.
What is the GCP identity platform?
The GCP Identity Platform is a set of tools and services that allows Google admin to manage and secure access to cloud-based resources. GCP does so using a central console. We can manage access and compliance over GCP services and third-party applications.
Any cloud identity is an IDaaS solution. GCP as cloud identity can be used as our IdP to enable users to access specified cloud apps. Organizations utilize the GCP Identity Platform to add customer identity and access management (CIAM) functionalities to their applications, services, and other products. This plays a role in user account security and secures Google Cloud scalability.
With Identity Platform, we can easily integrate a widely used, friendly, and adaptable authentication service into web and mobile apps, giving us valuable time to concentrate on developing products.
It additionally gives the power to manage third-party apps in one place. We can create, update, and delete profiles in one central location. The same will be reflected in our cloud apps.
Note: Google Cloud and Google Cloud Platform are used interchangeably. However, Google Cloud is a collection of cloud-based services and products provided by Google. This list includes the Google Cloud Platform.
Why GCP identity platform
GCP Identity platform secures accounts with single sign-on (SSO). Consider the traditional sign-up process. It usually uses cumbersome processes to complete. Chances are:
- Users opt to use a weak password that can be hashed or hacked
- Users tend to forget passwords; thus, tags such as forget passwords even create more complex steps to recover accounts.
- Users also often need to remember whether they already have an existing account, which drives up duplicate accounts in our system.
- The flow is too bulky to complete simply dropping off in the sign-up process.
The overall outcome of the such process generates more securing risk. Its process negatively impacts applications with reduced user conversion rates and increased maintenance costs.
Users generally choose a seamless, secure identity process that guarantees responsible data practices. GCP identity platform creates an easy-to-use, identity-preserving sign-up and signing process using password-less, token-based authentication methods. This allows seamless and easy sign-up or login to the apps without remembering a password. Take the following Google sign-in example, a scenario that we must have come across in web or mobile applications:
The GCP access process provide a formated Google sign-in button to create accounts as follows:
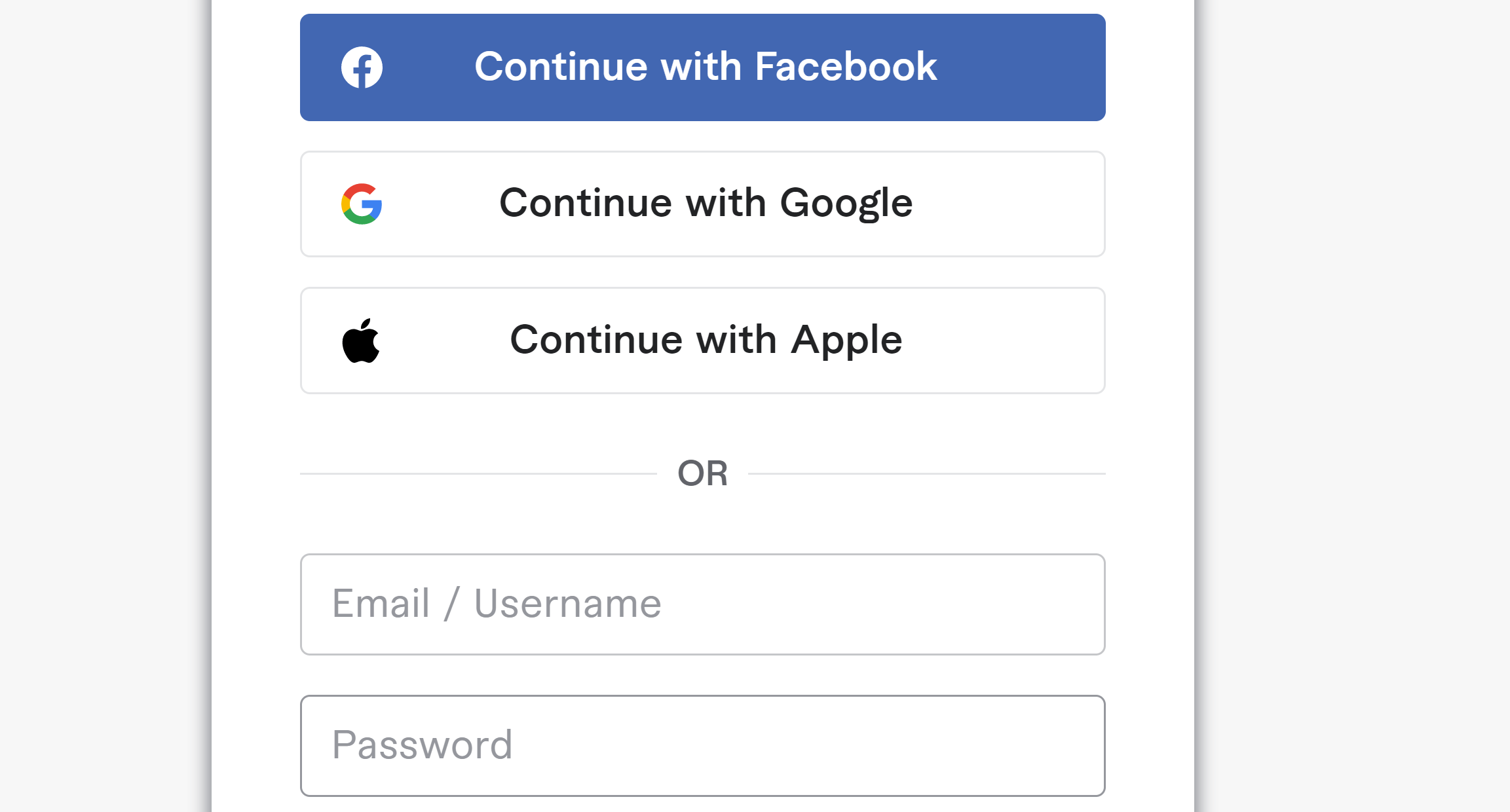
It automatically detects verified Google accounts and configures access with an SSO:
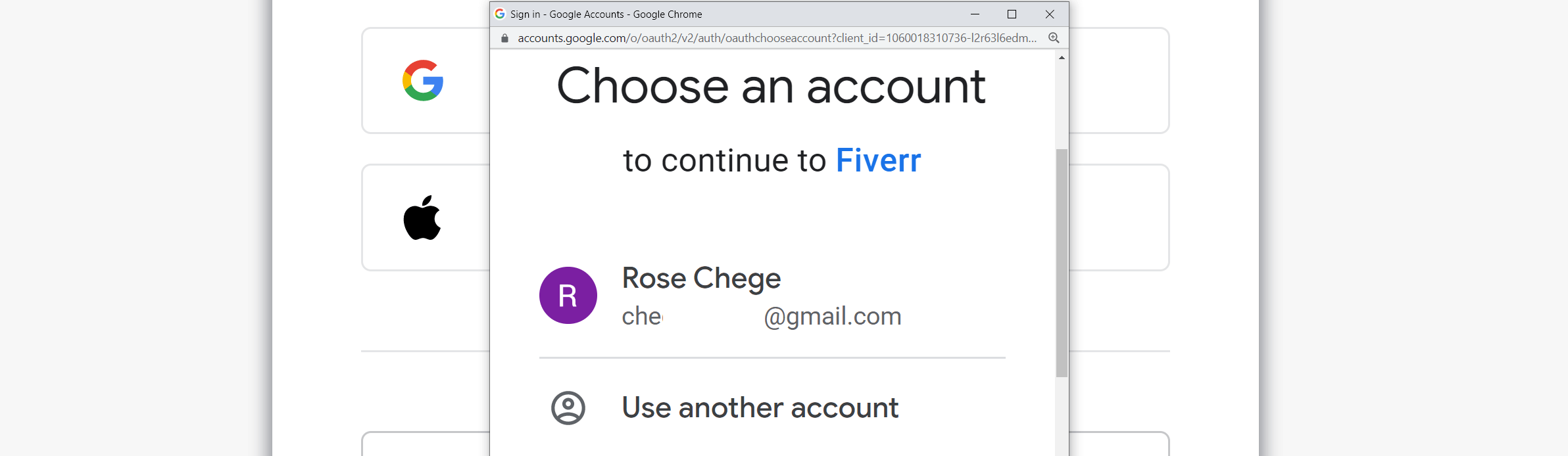
This process creates a seamless step for the user to access products and services. And if users sign out of the account, they don’t need a password to access back their account. GCP identity platform allows us to access with a single tap to mitigate account access frictions as follows:

Such identity processes create simple, safe platforms for the user. It makes it easier for organizations to:
- acquire users and thus increase conversion rates
- retain users
- Its security-preserving solutions minimize user-associated security risks
- No need to invent additional complex security management systems and thus mitigate costs
Organizations can take advantage and create secure access flows for their users. To get started, the Google Cloud Identity Platform offers a free tier of up to 50,000 monthly active users for authentication and up to 5,000 monthly active users for authorization. Beyond that, as secure user accounts and scale with confidence, pricing is based on the number of monthly active users and the features used.
Using the GCP identity platform
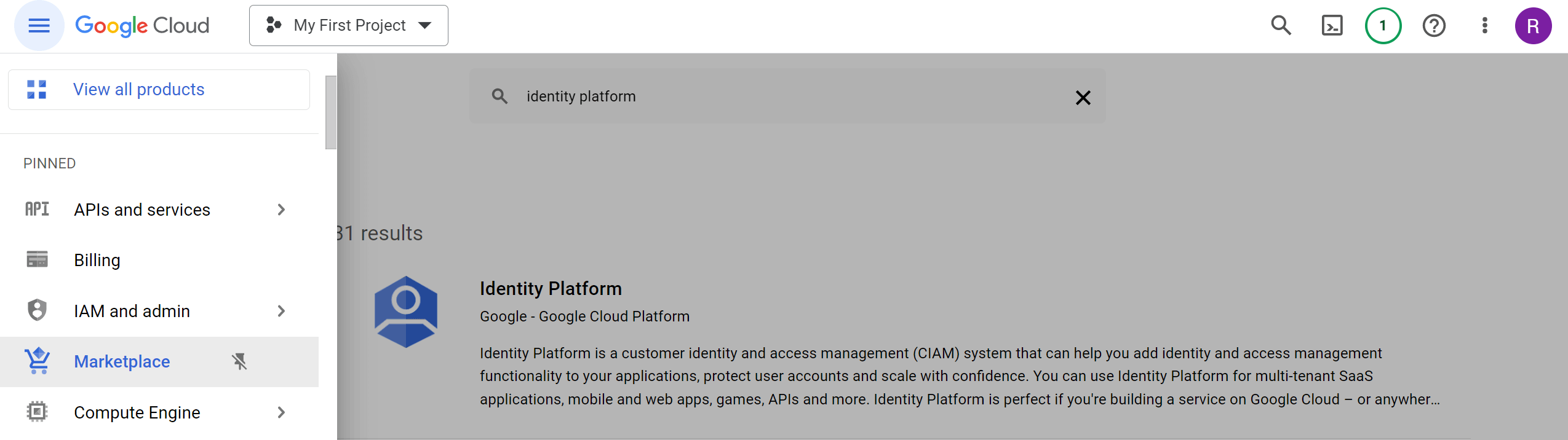
To get started with Google Cloud Identity Platform, sign up for a Google Cloud Platform account. Once we have an account, we can enable the Identity Platform services through the GCP console or API. Go ahead and search Identity Platform from the GCP marketplace.
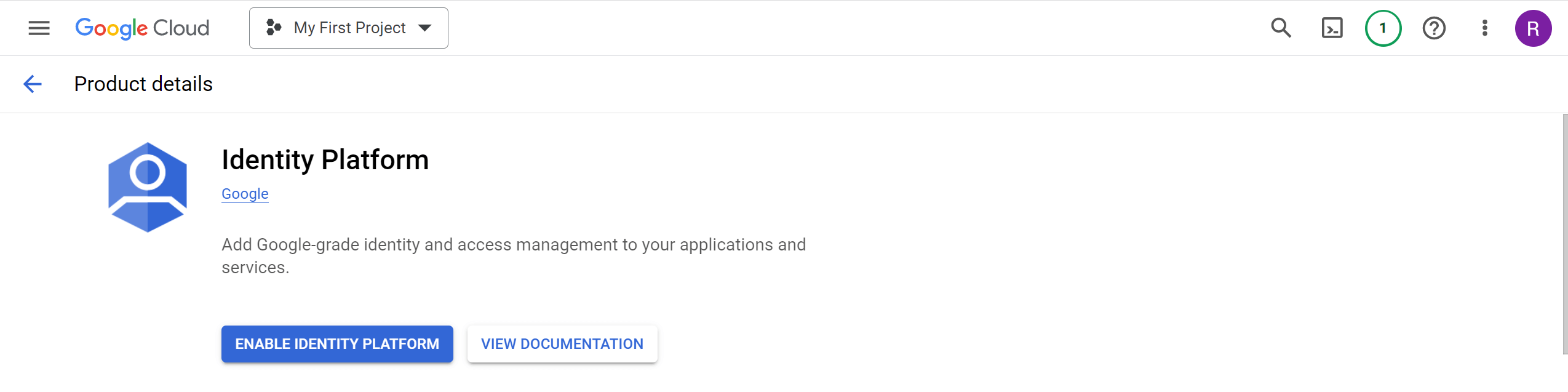
Once complete, ensure to configure Identity Platform in the GCP console using the Enable Identity Platform button as follows:
Next, navigate to the GCP console. We are ready to start using Identity Platform client and Admin SDKs for our apps and services.
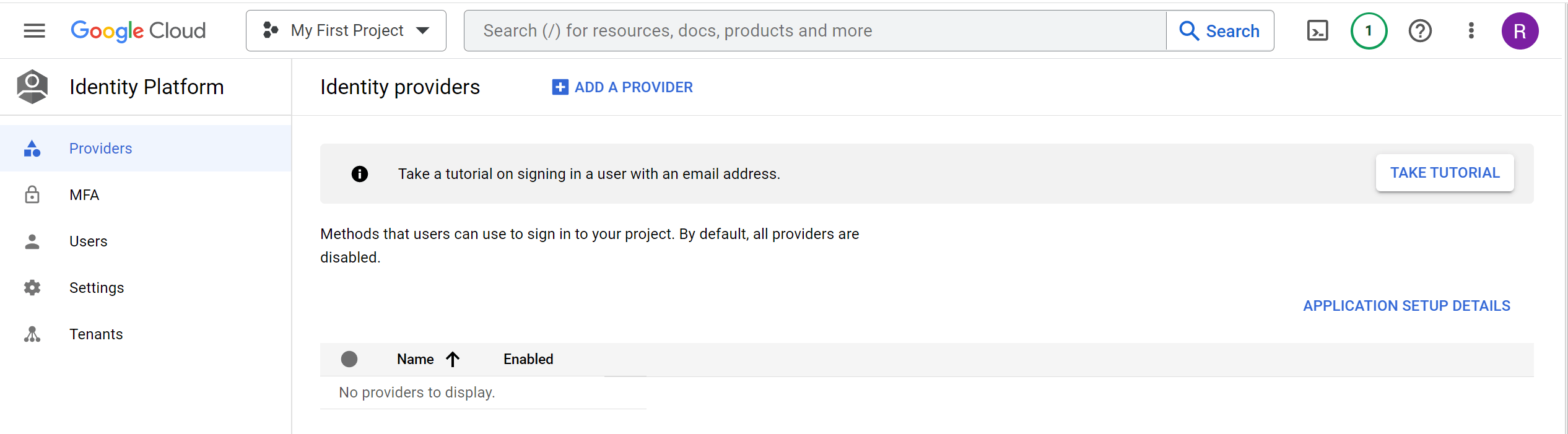
Once set, we can select the identity provider of choice. GCP provides a list of options we can implement as identity providers, such as SAML, Google, Twitter, Facebook Email/Password, and Phone, just to name a few. Using the provider of choice, we can use different SDKs such as Android, Node.js, Java, Python, JavaScript, and iOS and implement the providers on applications and services. Below is a simple example of how the medium implements identity providers for its users
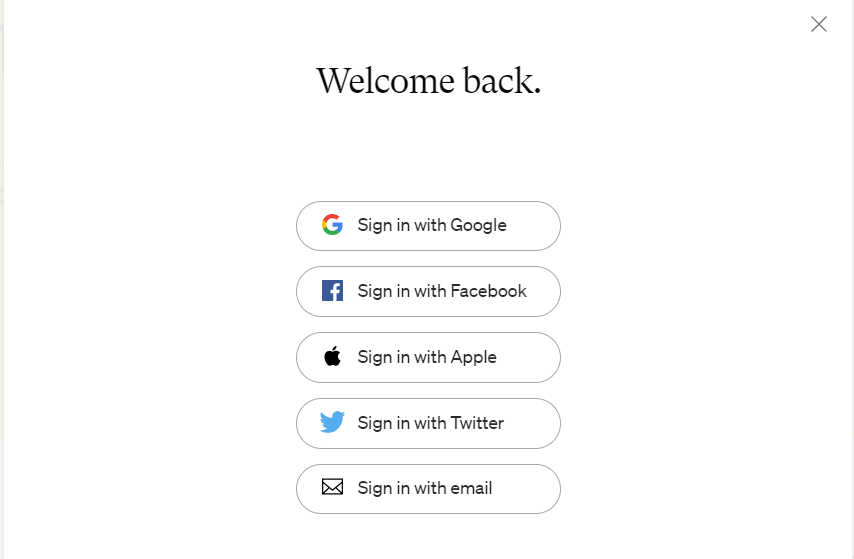
Google Cloud identity platform alternatives.
Many vendors provide IDaaS-related services, the Google Cloud identity platform being one of them. To choose a desirable IDaaS platform, consider the following:
- It must provide services from a cloud infrastructure. This reduces the overall cost of creating and managing In-House servers for keeping IDaaS in check. Cloud-based services are a good alternative for maintaining scalable IDaaS operations.
- Always ensure the vendor can provide a host of features necessary for our organization. We should confirm that we only pay for the features we use to reduce costs further.
- The ideal IDaaS should have excellent geographical reach to allow an organization to spread its products and services globally.
- Selected IDaaS services should be compatible with organization’s scope to ensure seamless integration.
- Ensure the selected IDaaS vendor has great customer support. We can contact them for any issues with availability to resolve them earliest. This reduces any delays and substantial impending losses on our side.
The common Google Cloud identity alternatives we can choose are:
- Okta - Okta supports authentication protocols, with its main feature being password-less sign-on, Multifactor authentication, API access management, etc.
- Ipsidy - provides IDaaS services and biometric identifications for organizations and users.
- IBM Cloud Identity - developed by IBM for user authentication, Frictionless registration, authorization, user management services, etc.
- Microsoft Azure Active Directory - a product of Microsoft. It’s a cloud-based identity platform for user management services.
- PingIdentity - creates a digital identity to seamlessly and securely connect any user and third-party services.
- Auth0 - is adaptable authentication and authorization platform for access management
Conclusion
Google Identity Services are simple, safe, and privacy-preserving solutions for signing up or signing in users to our platform. Data security posture management (DSPM) provides us with insights into the access controls to quickly detect any potential risks and vulnerabilities. Identity Services creates a secure pipeline that ensures user data is handled with responsible data practices while minimizing any potential security threat. They require minimum code implementation and no password risks associated with them. They create consistency across platforms that promotes user retention and conversion rates.
More Related Articles:
-

Understanding the Concept Cloud Managed Data Center Services
Managing an organization’s data can be costly and time-consuming, and there are so many security risks and vulnerabilities to consider while
Jul 21, 2023
-

Understanding the Concept of Data Management Cloud
We are encouraged to have a data management strategy because we could be welcoming damaging risks into our businesses without it. Much business data
Jul 21, 2023